wifidog+authpuppy搭建WiFi 认证平台
0:前提
其实搭建认证环境都是基础,重要的是要对WiFidog的代码进行详细的研究,了解清楚wifidog与authpuppy之间进行了哪些数据交互,WiFidog的程序框架及iptables的建立及生效规则,这才是重点。WiFidog和之前nodogsplash的代码90%是一样的,只是之前没有研究nodogsplash的外部认证机制。
WiFidog可以通过外部认证来控制用户的上网行为,此处的外部认证接口就是:authpuppy。
1:authpuppy安装之前准备
在安装authpuppy的过程遇到很多问题,但是都能根据网上其他朋友的提示可以搞定,我将自己想要的配置文件copy上来。
[root@localhost /etc]$cat host.conf
multi on
order hosts,bind
[root@localhost /etc]$cat hosts
127.0.0.1 localhost.localdomain localhost
127.0.0.1 authpuppy.localhost
::1 localhost6 localhost6.localdomain localhost6 localhost6.localdomain6
之后就是 httpd相关的配置文件:
/etc/httpd/conf]$cat httpd.conf
同时常用的命令如下:
service httpd restart,service mysqld restart等
其配置文件中主要就是配置一个虚拟目录.其配置内容如下:
<VirtualHost *:80>
ServerAdmin webmaster@test
ServerName authpuppy.localhost
ServerAlias authpuppy.test
DocumentRoot "/var/www/"
DirectoryIndex index.php
<Directory /var/www/authpuppy/web/>
Options Indexes FollowSymLinks MultiViews
AllowOverride All
Order allow,deny
allow from all
</Directory>
Alias /sf /var/www/authpuppy/lib/vendor/symfony/data/web/sf
<Directory "/var/www/authpuppy/lib/vendor/symfony/data/web/sf">
AllowOverride All
Allow from All
</Directory>
ErrorLog /var/log/httpd/error.log
# Possible values include: debug, info, notice, warn, error,crit,
# alert, emerg.
LogLevel warn
CustomLog /var/log/httpd/access.log combined
</VirtualHost>
[root@localhost /etc/httpd/conf]$cat httpd.conf
其中可以看出:
ServerName authpuppy.localhost
DocumentRoot "/var/www/" #web的根目录
DirectoryIndex index.php #访问的主页http://192.168.0.142/authpuppy/web/index.php
<Directory /var/www/authpuppy/web/> #authpuppy的目录位置
Options Indexes FollowSymLinks MultiViews
AllowOverride All
Order allow,deny
allow from all
</Directory>
authpuppy的目录位置及结构如下:
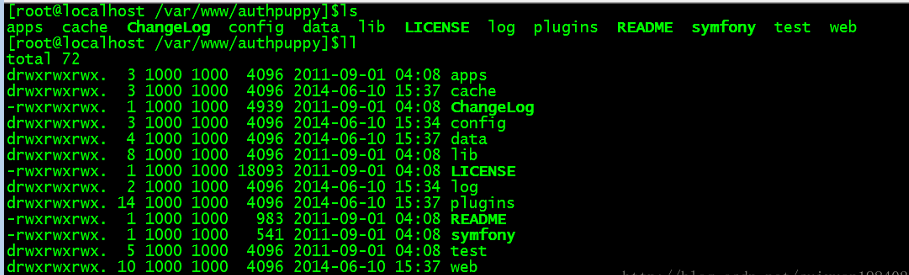
建立好上面的环境之后,下面就要建立MySQL数据库。建立好的数据如下:
[root@localhost ~]$mysql
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 813
Server version: 5.1.47 Source distribution
Copyright (c) 2000, 2010, Oracle and/or its affiliates. All rights reserved.
This software comes with ABSOLUTELY NO WARRANTY. This is free software,
and you are welcome to modify and redistribute it under the GPL v2 license
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| authpuppy |
| mysql |
+--------------------+
3 rows in set (0.01 sec)
mysql> use authpuppy;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+---------------------------+
| Tables_in_authpuppy |
+---------------------------+
| ap_applicable_policies |
| ap_connection_policies |
| ap_node_authenticators |
| ap_node_policies |
| ap_node_user_bypass |
| ap_plugin_config |
| ap_plugins_migrations |
| ap_user |
| ap_user_remember_me |
| connections |
| migration_version |
| nodes |
| sf_guard_forgot_password |
| sf_guard_group |
| sf_guard_group_permission |
| sf_guard_permission |
| sf_guard_remember_key |
| sf_guard_user |
| sf_guard_user_group |
| sf_guard_user_permission |
+---------------------------+
20 rows in set (0.00 sec)
mysql> slect * from ap_user;
ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near 'slect * from ap_user' at line 1
mysql> select * from ap_user;
+----+----------+--------------------------+--------------------+---------------------+------------------------------------------+--------+----------------+
| id | username | password | email | registered_on | validation_token | status | username_lower |
+----+----------+--------------------------+--------------------+---------------------+------------------------------------------+--------+----------------+
| 1 | suiyuan | H9hK9mgDAXdJnkYghQczkQ== | suiyuan626@163.com | 2014-06-10 16:05:25 | eda2838b1543e16fcfd7da6064886be67c544042 | 5 | suiyuan |
| 4 | xue | H9hK9mgDAXdJnkYghQczkQ== | xue626@163.com | 2014-06-10 17:04:07 | 117b0cd467900c59b9e60bb52719ce3551d321ce | 5 | xue |
+----+----------+--------------------------+--------------------+---------------------+------------------------------------------+--------+----------------+
2 rows in set (0.00 sec)
mysql>
其中上面是创建的俩个用户,是通过authpuppy的管理界面来创建的,用户在认证的时候只有输入正确的用户名及密码才能才算认证通过。同时如果不创建数据库,在启动authpuppy的时候会告诉缺少相应的文件目录。
3:安装过程
由于我们已经安装成功了,安装的过程中没有怎么抓图。
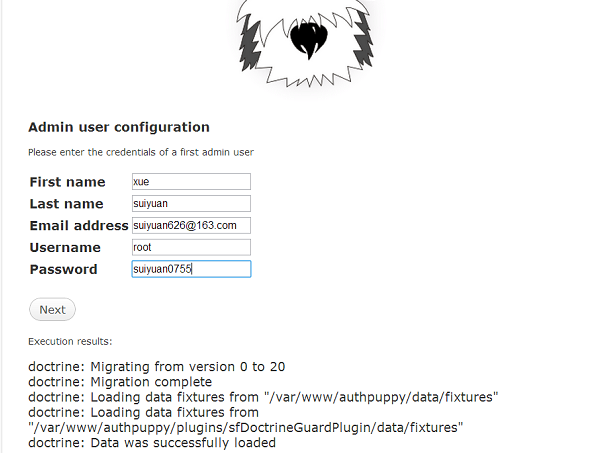
其中过一定要记住上面的用户名及密码,后面登陆的时候要用到,最好也写一个邮箱地址,如果忘记密码也可以找回来。
当安装成功之后访问:http://192.168.0.142/authpuppy/web/index.php
如下界面:
输入之前的用户名及密码(第二张图片上面的用户名及密码)。登陆之后的界面如下:
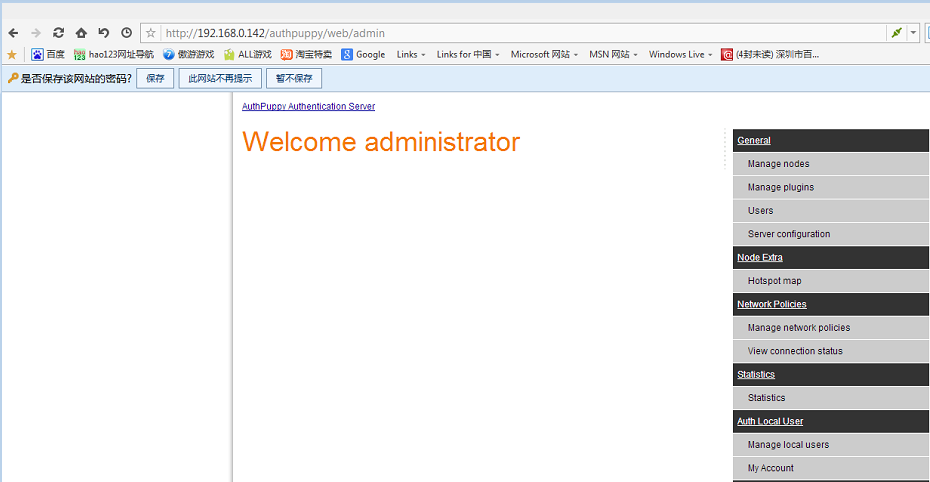
之后就可以安装插件,现在随便看看几个菜单。
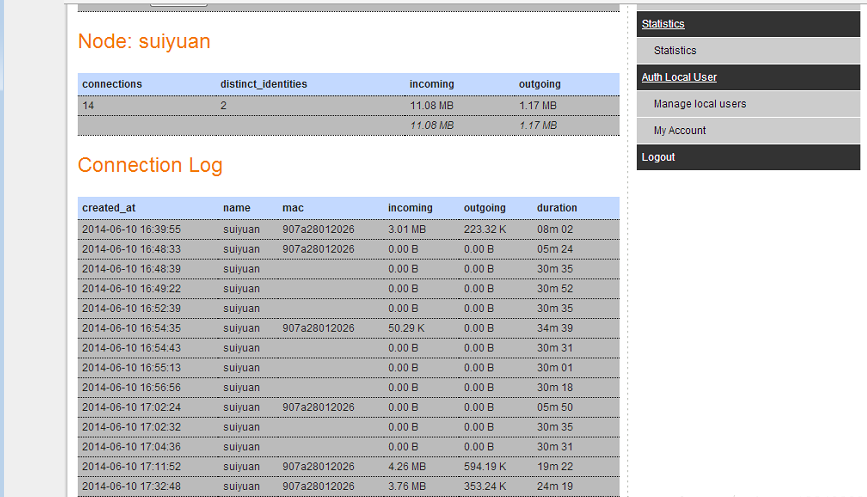
上面就是数据库里面创建的用户suiyaun(用户已此用户名进行登陆认证的)的上网的一些信息。
wifidog运行时的配置文件,其实配置文件只需要几个关键的参数就可以运行。
# WiFiDog Configuration file
GatewayID 123456789
ExternalInterface eth0
GatewayInterface br0
HtmlMessageFile /opt/wifidog/etc/wifidog-.html
AuthServer {
Hostname 192.168.0.142
SSLAvailable no
Path /authpuppy/web/
}
CheckInterval 60
# The timeout will be INTERVAL * TIMEOUT
ClientTimeout 5
# Parameter: TrustedMACList
# Comma separated list of MAC addresses who are allowed to pass
# through without authentication
#TrustedMACList 00:00:DE:AD:BE:AF,00:00:C0:1D:F0:0D
FirewallRuleSet validating-users {
FirewallRule allow to 0.0.0.0/0
}
FirewallRuleSet known-users {
FirewallRule allow to 0.0.0.0/0
}
FirewallRuleSet unknown-users {
FirewallRule allow udp port 53
FirewallRule allow tcp port 53
FirewallRule allow udp port 67
FirewallRule allow tcp port 67
}
FirewallRuleSet locked-users {
FirewallRule block to 0.0.0.0/0
}
本文章由 http://www.wifidog.pro/2014/12/16/wifidog-authpuppy%E6%90%AD%E5%BB%BA.html 整理编辑,转载请注明出处