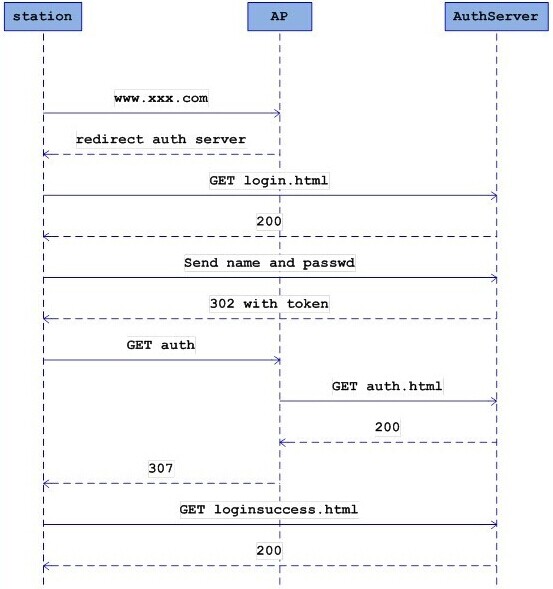
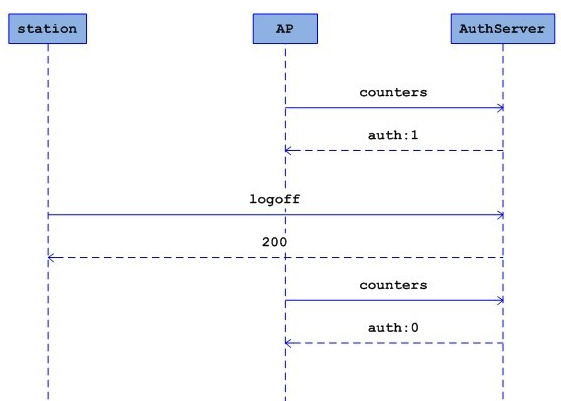
Wifidog was designed as a replacement to existing captive portal solutions which we felt didn't fit the needs of next generation community groups. Specifically, we wanted both personalized and community wide content for each hotspot, no pop ups, no client software and centralized management. Mainly as a replacement for portals currently using NoCat. A lot of other vendors use WiFiDog (especially the client) as a base for their solutions.
Wifidog’s Features
Main Features
Captive portal which lets hotspot owners communicate with their users (through the Content Distribution System).
Wifidog gateway was designed for and runs on GNU/Linux servers and embedded linux devices, e.g. Linksys WRT54G with OpenWRT. For a current list of supported devices and installation instructions please click Here.
Multilingual support (through browser detection and user selection) with the ability to add more languages using a .po editor (please see Language Translation for more details).Current implemented languages are:
English
French
German
Spanish
Italian
Greek
Portuguese (also Brazilian)
Swedish
Bulgarian
Japanese
Catalan
Maintain the client (hotspot users) connection by checking network activity through a ping command, instead of a javascript window (like used in NoCat). This allows PDAs and cellphones and other devices without javascript support to connect.
Support for differing types of hotspots:
Splash Only mode: Users are redirected to the portal, but do not have to login in order to use services
Normal Mode: Users are unique and must have a valid email address in order to open an account.
Users are able to create a working account directly from any hotspot. New users sign on from any hotspot, create their account and are granted access for 15 minutes to confirm an email. If they don't, they are disconnected and have to sign up again.
Hotspot/node monitoring by two way heart beating, so the central server always knows which hotspots/nodes are up, regardless of dynamic DNS, firewalls, etc.
Reports and Statistics including:
10 highest bandwidth consumers
10 most frequent users
10 most mobile users
Anoymised SQL data export (for academic research)
Breakdown of how many users actually use the network
Connection log
Content display and click through report
Graph on network use (per hour, weekday and month)
Individual user report, most popular nodes (by visit)
Network status information
Node status information
Registration log
User registration report
Automatic node creation (if the person creating the node has the relevant permissions and the feature is enabled).
Please see the Road Map for new features currently in development.
Most awaited features are:
User classes
Bandwidth limiting per class
Bandwidth limiting per router
Port blocking per class
Apply policies based on time of day
Auth server (Current)
Node-specific content features. Wifidog-auth has a very cool local content architecture.
RSS feed support (optional, with magpierss), one feed per node (url stored in the database, works great, but no gui to edit it yet) and one network-wide RSS feed.
Configuration and integration
No need to set any path in the web server config files
All paths are editable from the config file
Quick setup: the network name, url, default RSS, and similar data are set from the config file, and will be displayed as needed throughout the system.
Can import all users and passwords from a NoCat password file [WWW] More info].
Development
Demo page to let people to hack on it more easily
Database abstraction layer with very nice debugging features (just append true at the end of the call and you'll see the query, the results, the query plan, and the number of affected rows. Porting to another database only requires porting one file. Currently uses Postgres.)
User management (end user)
Users can create and activate accounts without admin intervention. The user will be granted a 15 minute grace period after signing up in order to retrieve and validate his email.
Users can request that the server re-send the validation email
Users can change their passwords
Users who forget their username can have it mailed to them.
Users who lose their password can ask the system to generate a new one and mail it to them.
Email must be valid but isn't displayed in order to preserve user privacy.
Users can login using either email or username
Enforces (politely) that duplicate email addresses are not allowed in the database
Logging and monitoring
MAC address logging (in case it is a legal requirement in your country)
Sends the original url before redirecting to the central server in order to allow linking on the portal page
Multi-language support
Script and sql execution time breakdown. Already implemented, just needs to be packaged to be usable by the templates.
Reports and Statistics
Gateway (Current)
Supports using backup auth servers if the primary one doesn't respond.
Runtime query interface
One rule to jump in, one to jump out rejects, one to jump out accepts
Detects the IP address of a network interface automatically, instead of specifying it separately in the configuration file.
Sourceforge
You can also take a look at Sourceforge Feature Requests page or add your own new requests.
本文章由 http://www.wifidog.pro/2014/12/08/5.html 整理编辑,转载请注明出处