wifidog认证
前段时间使用wifidog进行wifi强制认证,现在做个小结。
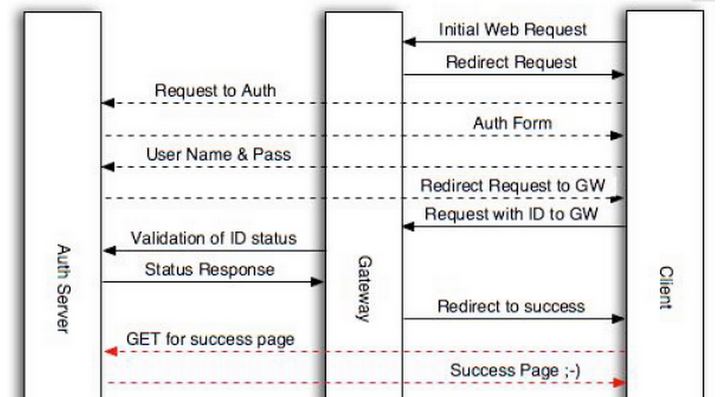
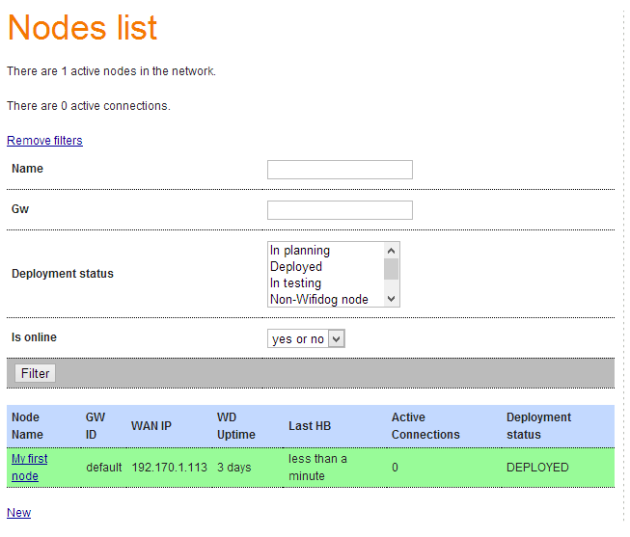
- 首先简单说说wifidog认证的过程
客户端首次连接到wifi后,浏览器请求将会被重定向到:
login/?gw_address=%s&gw_port=%d&gw_id=%s&url=%s
验证通过后,客户端被重定向到网关,url格式如下:
http://网关地址:网关端口/wifidog/auth?token=xxx
wifidong会启动一个线程周期性地报告每一个用户的状态信息,并通过如下地址发送给认证服务器:
auth_server:/auth/?stage=
ip=
mac=
token=
incoming=
outgoing=
认证服务器根据该状态信息决定是否允许该用户继续连接,并回复网关,回复格式为:Auth:状态码,
如:Auth:1
常用状态码:
0:AUTH_DENIED,表示拒绝
1:AUTH_ALLOWED,验证通过
验证通过后,将重定向到如下地址:
portal/?gw_id=%s
wifidog的ping协议
wifidog通过ping协议将当前状态信息发送给认证服务器,发送地址为:
http://auth_sever/ping/?
gw_id=%s
sys_uptime=%lu
sys_memfree=%u
sys_load=%.2f
wifidog_uptime=%lu
认证服务器须返回一个“Pong”作为回应。 实战应用
struts配置文件:
/Login/index.jsp
/error.jsp
Action方法
public String login() {
try{
System.out.println("login start!");
System.out.println("gw_port:"+gw_port);
System.out.println("login end!");
}
catch(Exception e)
{
e.printStackTrace();
return INPUT;
}
return "success";
}
public void ping() {
try{
System.out.println("ping start!");
System.out.println(gw_id);
ServletActionContext.getResponse().getWriter().write("Pong");
System.out.println("ping end!");
}
catch(Exception e)
{
e.printStackTrace();
}
}
public void portal() {
try{
System.out.println("portal start");
System.out.println("protal"+token);
ServletActionContext.getResponse().sendRedirect("/demo/listAction");
System.out.println("portal end");
}
catch(Exception e)
{
e.printStackTrace();
}
}
public void auth() {
try{
System.out.println("auth start!");
System.out.println("mac"+mac);
System.out.println("stage"+stage);
System.out.println("token"+token);
ServletActionContext.getResponse().getWriter().write("Auth: 1");
System.out.println("auth end!");
}
catch(Exception e)
{
e.printStackTrace();
}
}
/Login/index.jsp代码:
<%
String path = request.getContextPath();
String basePath = request.getScheme()+"://"+request.getServerName()+":"+request.getServerPort()+path+"/";
DateFormat format=new SimpleDateFormat("yyMMddHHmmss");
String formatData=format.format(new Date());
int ramdom=new Random().nextInt(1000);
String token=formatData+ramdom;
if(session.getAttribute("token")==null)
session.setAttribute("token",token);
%>
<form method="GET" action='http://192.168.1.1:2060/wifidog/auth'>
<input type='hidden' name='token' value="<s:property value="#session.token" />" />
<input type='submit' value='Welcome!'/>
</form>
上面的192.168.1.1为网关的ip,2060为网关端口。
当然,完全可以在处理完login后直接跳到该地址。我们这里为演示其认证流程,故跳到该页面。
效果:
客户端连接到wifi后,打开任何连接均跳到上面的index.jsp中,点击"Welcome"后,跳到/demo/listAction,即我们的目标地址。此后点击其他连接将不再拦截。
提示:安装wifidog的路由器必须可以访问Internet,否则wifidog拦截失败,无法跳到我们设定的页面。
本文章由 http://www.wifidog.pro/2014/12/16/67.html 整理编辑,转载请注明出处